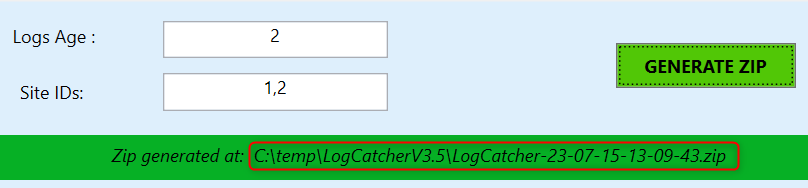
Download and save LogCatcherV3.5.zip from https://github.com/NL-Cristi/LogCatcher/releases/download/v3.5/LogCatcherV3.5.zip, view the Properties of the zip file and tick the Unblock checkbox and click Apply.
Please ensure that the execution of PowerShell scripts is enabled. If you're unsure whether script execution is enabled, open PowerShell and run the following command:
Get-ExecutionPolicy. If the result isRemoteSigned,Unrestricted, orBypass, then script execution is enabled regardless of whether your system is a Windows Client or Windows Server. If your system is Windows Server and the result isDefaultorUndefined, then PowerShell script execution is also enabled. In any other scenario, script execution in PowerShell is prohibited. If you want to enable PowerShell script execution, please refer to the steps below:Run PowerShell as an administrator and execute following command to set the PowerShell ExecutionPolicy to
RemoteSigned. This will allow PowerShell to execute scripts.Set-ExecutionPolicy -ExecutionPolicy RemoteSignedIf you encounter any errors with the execution of the above command, please proceed with the steps below:
- To allow script execution in Windows PowerShell, execute following commands in an elevated CMD or PowerShell window:
REG ADD HKLM\SOFTWARE\Policies\Microsoft\Windows\PowerShell /v EnableScripts /t REG_DWORD /d 1 /f REG ADD HKLM\SOFTWARE\Policies\Microsoft\Windows\PowerShell /v ExecutionPolicy /d "RemoteSigned" /f - To allow script execution in PowerShell Core (Cross-platform PowerShell), execute following commands in an elevated CMD or PowerShell window:
REG ADD HKLM\SOFTWARE\Policies\Microsoft\PowerShellCore /v EnableScripts /t REG_DWORD /d 1 /f REG ADD HKLM\SOFTWARE\Policies\Microsoft\PowerShellCore /v ExecutionPolicy /d "RemoteSigned" /f - After restarting PowerShell, these changes will take effect.
- To allow script execution in Windows PowerShell, execute following commands in an elevated CMD or PowerShell window:
LogCatcher
Prerequisites
End steps
Run PowerShell as an administrator, navigate (using the cd command) to the directory where you extracted LogCLogCatcherV3.5.zip, then execute the following command to start log collection:
.\LogCatcher.ps1Note: The first time you run this script, you may need to click Accept to agree to the User License Agreement.
In the pop-up LogCatcher interface, specify the number of days covered by the logs you want to capture in the Log Age field. The default is 2 days. Input the IIS website IDs you want to capture in the Site IDs field. By default, it will capture all IIS websites. Then click GENERATE ZIP to begin capturing the logs.
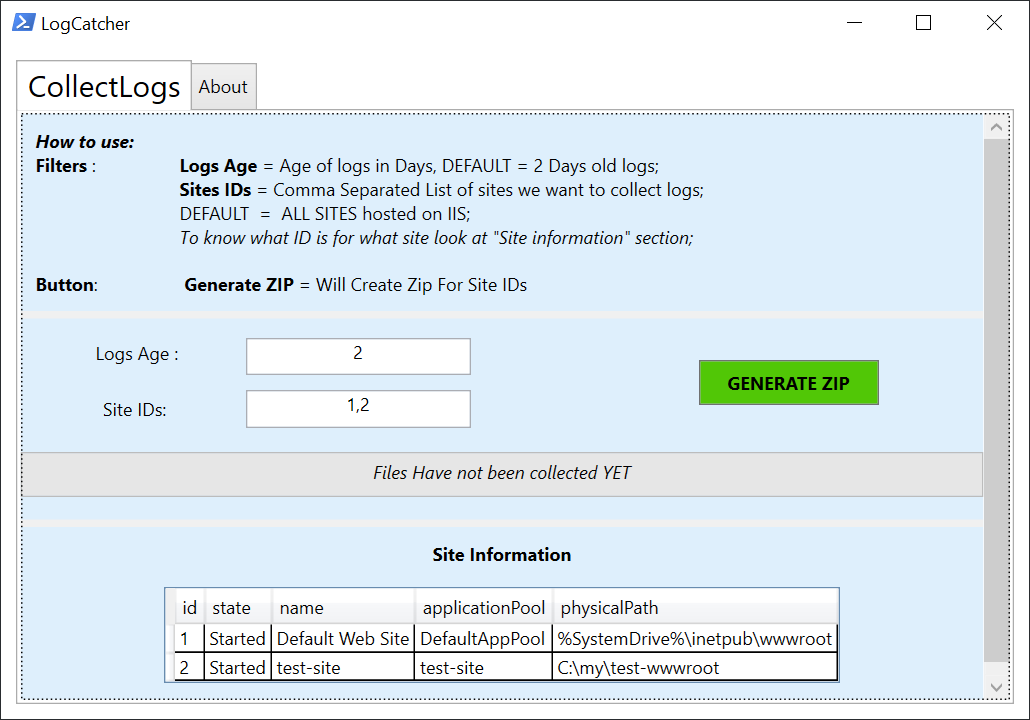
Wait for LogCatcher to capture the logs. The whole process will take some time depending on the number and size of the logs to be captured. Errors may appear in PowerShell during this process, but you can ignore them. Upon completion, LogCatcher will package all the logs into a ZIP file and display the path of the ZIP file on the interface.