- Download ProcDump from https://learn.microsoft.com/en-us/sysinternals/downloads/procdump and extract the files.
Capture IIS Application Pool (Worker Process) dumps manually using ProcDump
Prerequisites
Main steps
Press the
Win key + Ror right-click the Start menu and click on Run to open the Run dialog. Then, type inetmgr and press Enter to open the IIS Manager.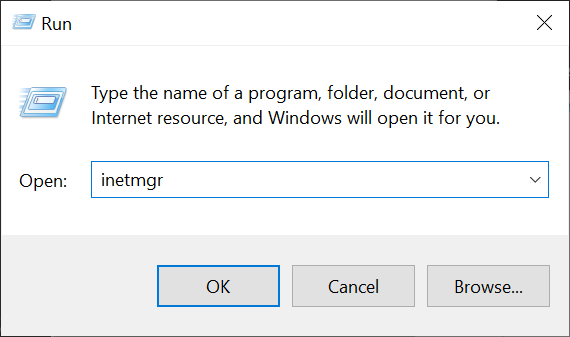
In the left Connections panel of the IIS Manager, click on the server root node, then double-click Worker Processes to view all currently running IIS worker processes on the server.
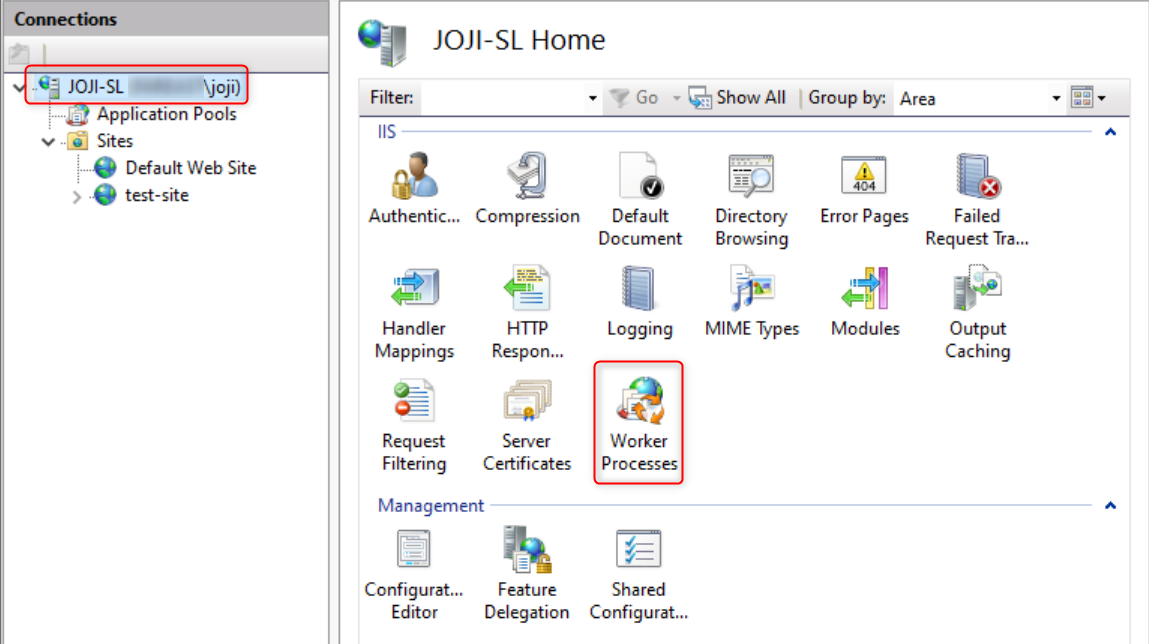
Identify and remember the Process ID corresponding to the Application Pool from which you wish to capture a dump.
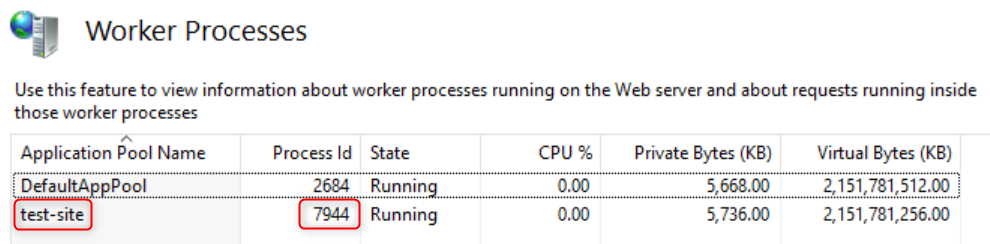
If there are multiple Worker Processes running and you're unsure which Application Pool corresponds to your IIS website of interest, you can refer to the following steps to identify the correct Application Pool.
Press the
Win key + Ror right-click the Start menu and click on Run to open the Run dialog. Then, type inetmgr and press Enter to open the IIS Manager.
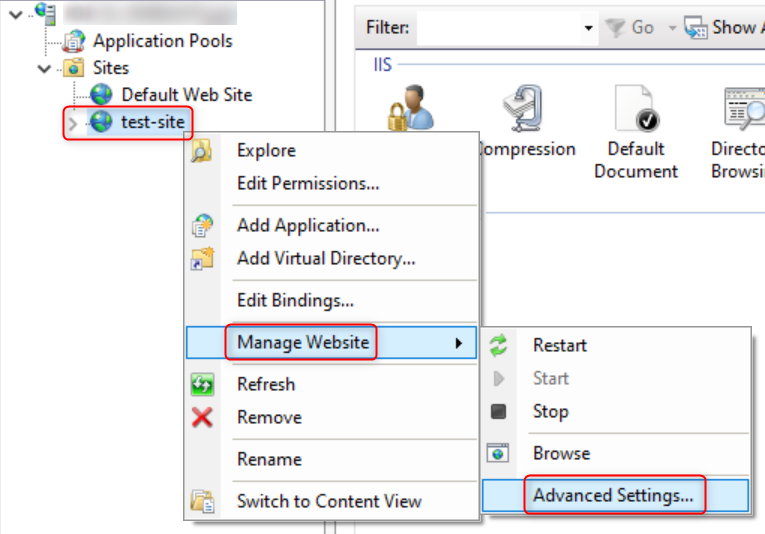
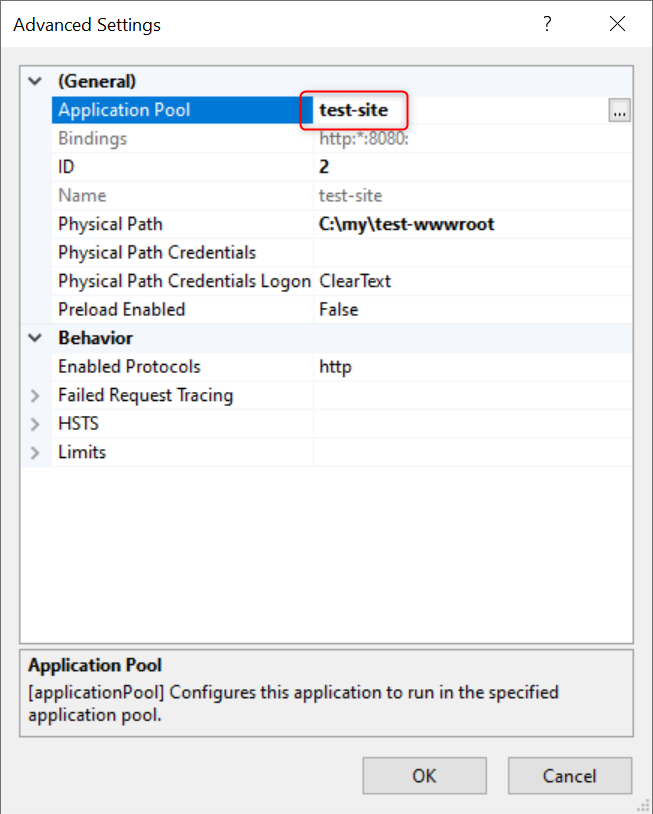
Right-click on the website for which you want to retrieve the Application Pool, then select Manage Website -> Advanced Settings.... In the Advanced Settings window that pops up, you will find the name of the Application Pool corresponding to the website.
Run CMD or PowerShell with administrator privileges. Change directory (CD) to the location where you've unzipped ProcDump, then run the command below, replacing
<PID>with the Worker Process id you identified in the previous step. For example, if the process id was 7944, then runprocdump.exe -ma 7944 -n 3 -s 2 -accepteula.procdump.exe -ma <PID> -n 3 -s 2 -accepteulaThis command will consecutively capture 3 full user dumps, with a 2-second interval between each dump. If you want to adjust the number of dumps being captured, you can modify the parameter following
-n. If you want to adjust the interval between each dump capture, you can modify the parameter following-s.Once ProcDump finishes capturing, the dumps will be generated in the current working directory. You can identify these dump files by observing the output of ProcDump for the filenames.
[11:57:59] Timed: [11:57:59] Dump 1 initiated: c:\temp\Procdump\w3wp.exe_230715_115759.dmp [11:58:00] Dump 1 writing: Estimated dump file size is 56 MB. [11:58:00] Dump 1 complete: 56 MB written in 0.9 seconds [11:58:03] Timed: [11:58:03] Dump 2 initiated: c:\temp\Procdump\w3wp.exe_230715_115803.dmp [11:58:04] Dump 2 writing: Estimated dump file size is 56 MB. [11:58:04] Dump 2 complete: 56 MB written in 0.3 seconds [11:58:07] Timed: [11:58:07] Dump 3 initiated: c:\temp\Procdump\w3wp.exe_230715_115807.dmp [11:58:07] Dump 3 writing: Estimated dump file size is 56 MB. [11:58:07] Dump 3 complete: 56 MB written in 0.3 seconds [11:58:07] Dump count reached.